Below is our recent interview with Purandar Das, CEO & Co-Founder at Sotero. Throughout his career, Purandar has been working on utilizing technology to solve complex business challenges. He adopts a pragmatic approach that enables businesses to leverage technology to achieve business goals and power growth.

Q: Purandar, could you start by giving us an overview of Sotero and its mission to help businesses in the current data-driven landscape?
A: Sotero is dedicated to revolutionizing data security. Our mission is to provide robust, seamless protection for data across all platforms. In this era where data is the most valuable asset, we focus on ensuring businesses can quickly and easily leverage their data while simultaneously keeping it secure and preventing inappropriate access. We approach cybersecurity from a data-centric or data-first mindset
Q: Sotero emphasizes data-centric cybersecurity, including Data Security Posture Management (DSPM). How does this approach empower organizations to secure their data more effectively?
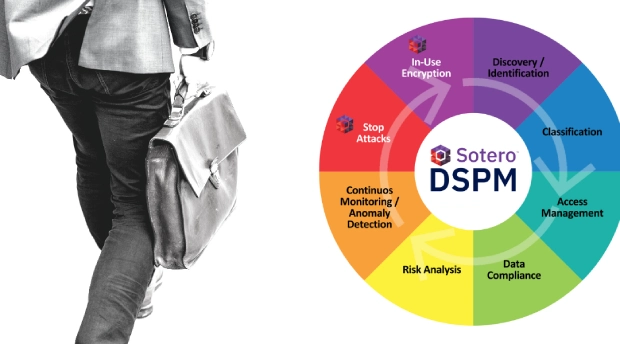
A: DSPM is at the heart of Sotero’s approach. It allows organizations to continuously monitor and manage their data security posture, identifying risks in real-time and driving rapid remediation before attackers can exploit it. This proactive stance ensures that data is always protected, at rest — in transit, and in use — even as threats evolve.
Q: In the context of the cloud environment, what strategies does Sotero implement to prevent data loss and breaches?
A: The cloud environment is one of the most complex environments to secure. Providing organizations with flexibility and agility in their operations is necessary, but also exposes them to many cyber threats and potential misconfigurations that might increase risk.
In the cloud environment, Sotero employs a multi-layered strategy. This includes securely encoding proprietary data, access control, and continuous monitoring, ensuring that data remains secure and breaches are prevented effectively without hindering the usefulness of the data to authorized users.
Q: Ransomware attacks are a major concern for businesses. Can you elaborate on how Sotero creates a ‘foolproof’ solution to this threat by enhancing an organization’s security at the data level?
A: Our solution to ransomware is comprehensive. With the speed of ransomware development and evolution, traditional detective AV, which relies on signatures, cannot keep up. We use advanced algorithms to detect anomalies, identifying threats early and isolating them swiftly. This approach prevents ransomware attacks and minimizes their impact, ensuring business continuity. Effectively, Sotero adds that critical last line of defense at the data level to ensure comprehensive security.
Q: What sets Sotero apart in the field of data security, especially aspects that might not be widely known?
A: Our unique blend of advanced technology and user-centric design sets Sotero apart. We aim to strike the balance of usability and protection by offering cutting-edge security features powered by machine learning, all managed through a single unified interface. Our protection works in the background, maintaining protection for all users with minimal management overhead.
Q: Could you discuss how Sotero’s upcoming data breach immunity campaign is a game-changer in closing the loop on data exfiltration?
A: Our data breach immunity campaign shifts away from traditional DLP approaches and focuses on ‘closing the loop’ on data exfiltration. DLP focuses 100% on keeping data from leaving, our solution assumes there is a risk that the data will exit the company’s control and extends the protection outside of the organizational boundaries. Sotero keeps the data unusable and secure to unauthorized individuals no matter where it resides, even if stolen.
Q: How does Sotero address the increasing concerns around insider threats, especially in platforms like Microsoft SharePoint?
A: Sotero implements advanced encryption and granular access control. Our solution encrypts sensitive data within SharePoint, making it inaccessible to unauthorized users, including insiders with elevated privileges. We go beyond standard access permissions, providing detailed control over who can access what data. This approach not only protects against external threats but is crucial in mitigating the risks posed by insider threats, ensuring that sensitive information remains secure even if access credentials are compromised.
Q: Could you elaborate on the use case of integrating Sotero with SharePoint in an organization to mitigate risks of data breaches, unauthorized data access, and ransomware attacks?
A: Integrating Sotero with SharePoint significantly elevates data security. Our advanced encryption shields critical financial data from breaches, while our granular access control ensures that only authorized personnel access specific datasets, reducing the risk of internal misuse. Moreover, Sotero’s active ransomware protection adds a vital layer of defense against such attacks, safeguarding the company’s SharePoint environment. This integration results in a robust security posture, effectively mitigating risks of data breaches, unauthorized access, and ransomware while maintaining integrity and confidentiality, which is critical for sensitive data such as financial or health-related information.
Q: How does Sotero’s solution integrate with existing enterprise systems to enhance overall security posture?
A: Sotero is designed to integrate seamlessly with existing enterprise systems, enhancing the overall security posture by adding an extra layer of protection without disrupting existing workflows. We believe that security should not require major changes to infrastructure, but instead interoperate and build on the solutions and technologies your business already relies on.
Q: Finally, what future developments can we expect from Sotero in data security and protection?
A: Looking ahead, Sotero aims to continue innovating in data security. We’re exploring how to push the boundaries of AI and machine learning to further enhance our security capabilities, ensuring we stay ahead of emerging threats.